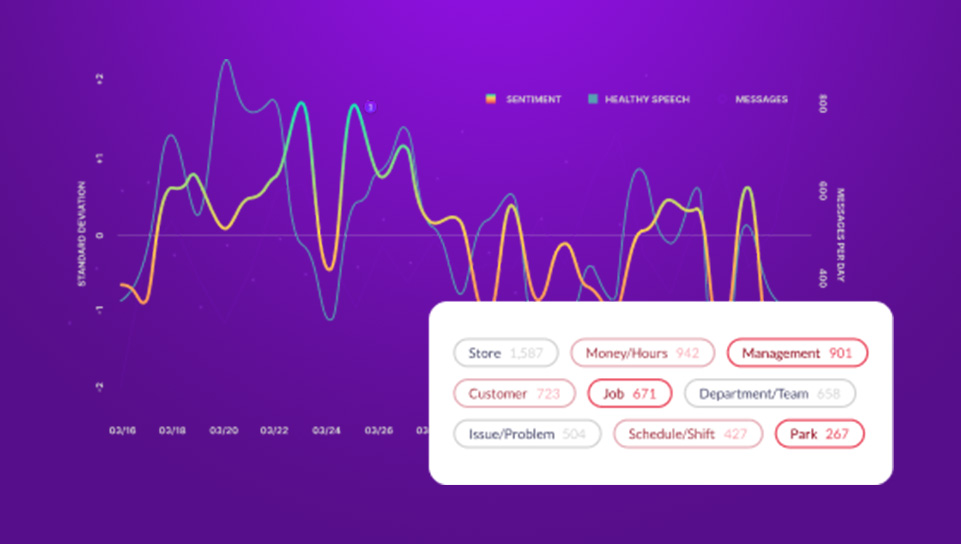
A Complete Guide to Microsoft Teams DLP
by Aware
Data loss prevention (DLP) is a data security methodology designed to identify and safeguard against the unsafe or inappropriate sharing, transfer, or use of sensitive data. A data loss prevention policy is a set of protocols and tools put in place by organizations as an overall strategy to prevent data breaches and leaks. Robust data security and compliance strategies that include solid DLP policies ensure companies can consistently safeguard data across multiple collaboration tools, including Microsoft Teams.
Contents
- What is Microsoft Teams’ DLP solution?
- Why is DLP essential for Microsoft Teams?
- What are Microsoft Teams’ in-built DLP features?
- What is a DLP policy and how to create one in Microsoft Teams
- Steps for creating a DLP policy for Microsoft Teams
- Examples of how DLP works in Microsoft Teams
- DLP reporting on Microsoft Teams
- Integrate with Aware for advanced AI-powered DLP
What is Microsoft Teams’ DLP solution?
For organizations using Microsoft Teams, DLP is integrated with Microsoft Purview data loss prevention to protect data within Microsoft Teams chats and channels. DLP policies are managed through the Purview compliance center portal, where sensitive information types are consistently classified across multiple workflows, including Exchange, SharePoint, OneDrive, and more. Purview’s compliance portal gives admins a single view to surface alerts from multiple sources for unified incident management.

Whitepaper: An IT Leader's Guide to Collaboration Compliance
Why is DLP essential for Microsoft Teams?
Microsoft Teams is an indispensable collaboration tool for a significant number of organizations. It promotes effective team communication and allows data to flow whether people are in the next office or on the other side of the world. However, the data it contains is a valuable asset that must be protected.
DLP is essential for Microsoft Teams admins to minimize these possible risks:
- Users sharing sensitive information on Teams channels: Teams facilitates real-time communications and file sharing. Some users may—inadvertently or intentionally—share sensitive data in ways that are not authorized. This information could include personally identifiable information (PII), financial records like payment card industry (PCI) data, or intellectual property. If shared on channels where unauthorized individuals or external guests may see, it could lead to leaks and compliance violations.
- Unintentional data leaks due to incorrect storage location: Teams allows users to share and store files within channels, chats, and SharePoint or OneDrive locations. If sensitive data is stored in a location with improper access controls, it could be exposed to unauthorized individuals and lead to data breaches.
- Third-party integrations introducing vulnerabilities: One of Teams’ attractive features is its ability to integrate with third-party apps and services. However, while these apps can enhance productivity, they can also introduce holes in security if not properly vetted and secured, leaving sensitive data open to unauthorized access or misuse.
Organizations that proactively adopt robust DLP policies to identify and protect data and enforce safe handling practices are more likely to prevent accidental or intentional data leaks in Microsoft Teams and other collaboration tools. DLP, compliance monitoring, and data security best practices ensure sensitive information remains protected within Teams.
Webinar: Controlling Collaboration Data
What are Microsoft Teams’ in-built DLP features?
Microsoft Teams integrates with Microsoft Purview DLP to bring several native features for sensitive data protection to the Teams environment.
- Detect sensitive data sharing: Teams DLP leverages sensitive information types as defined in Microsoft Purview Information Protection to detect when sensitive data is shared. Purview detects when PII, PCI and other financial records, health records, and intellectual property are shared in chat messages, channel conversations, and shared files.
- Managing access: DLP policies can be configured so that when sensitive data is shared in Teams, protective actions are triggered, and data protections are enforced. These actions can include blocking the message or file from being shared, notifying the user of policy tips, and restricting access to sensitive content for unauthorized end users or external guests.
- Test mode for DLP policies: Administrators can test and validate their DLP policies in a non-disruptive test environment before putting them into production for enforcement. Test mode simulates policy violations without really blocking or restricting content, giving admins the ability to assess their policy’s effectiveness and impact.
- Integrated reporting: The centralized Microsoft Purview compliance portal surfaces DLP alerts for policy violations in Teams to provide a unified view for incident reports and management. Admins can access detailed reports on DLP policy matches, overrides, and false positives, giving them tools to monitor and analyze data risks in Teams.
Checklist: Simple Steps to Collaboration Security
Native DLP features in Teams, combined with the Purview integration, enable companies to establish data protection strategies for their Teams environment. Through leveraging data detection, access management, policy testing, and centralized reporting, admins can be proactive about mitigating risks, preventing data breaches, and maintaining compliance.
What is a DLP policy and how to create one in Microsoft Teams
DLP policies are rules and actions meant to identify, monitor, protect, and preserve data from unauthorized access, sharing, misuse, and loss within an organization’s systems and applications.
Case Study: A DLP policy is designed to prevent the mishandling of data. For example, this large technology service company works with clients who employ external consultants with access to highly sensitive projects. Those consultants communicate through separate devices—one for their internal projects and another for the tech company’s clients. The company has concerns about the risk exposure of the consultants potentially sharing intellectual property on devices they cannot monitor. They use Aware to monitor how and where all data is shared and alerts them when unauthorized information is shared, providing the conversation’s context so they understand the reason for the policy violation. With this knowledge, the technology company implements workflows to hide potentially sensitive info from unauthorized users and coaches the broader organization on sharing protocols.

Whitepaper: Collaboration Data Governance
Steps for creating a DLP policy for Microsoft Teams
- Choose the data to monitor: Select the data types that are sensitive and subject to monitoring and protection. These could be credit card numbers, social security numbers, patient health information (PHI), or custom data patterns specific to your company. Microsoft provides predefined templates for common data types, or you can create customized sensitive data types.
- Define administrative scope: Determine the scope of your DLP policy by selecting the users, groups, and administrative units where the policy will apply. You can target specific departments or teams within your organization for compliance purposes or go broader to encompass everyone.
- Choose locations to monitor: Specify the Microsoft Office 365 locations where the DLP policy will monitor for sensitive data. For Microsoft Teams, select “Teams chat and channel messages” to monitor conversations and shared files within Teams.
- Set policy conditions: What conditions will trigger your DLP policy? For example, if data is shared with someone outside your organization, or if certain data like a social security number or credit card number is detected within Teams messages or files, your DLP policy comes into play.
- Configure policy actions: When the policy conditions are met, what actions will happen? For Microsoft Teams, you can select blocking or restricting access to sensitive content, notifying the user of policy tips, or encrypting the content in Microsoft 365 locations.
- Test and deploy the policy: Before enacting the DLP policy in your live environment, use test mode to ensure their effect and impact are as you expect. Once you’re satisfied with the outcome of the test, deploy the policy in the live environment.
Creating and implementing DLP policies for Microsoft Teams gives administrators tools to identify and protect information and mitigate the risks it contains. The policies enable enforcing data handling protocols and prevent data leaks across collaboration in the Teams environment.

Checklist: Information Governance for Collaboration
Examples of how DLP works in Microsoft Teams
DLP policies monitored through the Microsoft Purview compliance portal can safeguard sensitive information found in Microsoft Teams. Here are three scenarios for how DLP policies may work in different situations.
Example 1: Protecting sensitive data in Teams messages
An employee is having trouble logging into the company software where credit card information is typically managed and updated while a customer is on the phone. To save the number to update when the glitch is resolved, the employee shares the credit card information in Teams with a trusted coworker. The organization’s DLP policy kicks in, blocking the content and notifying the employee that their message violated the organization’s DLP policy. They may be given the option to override the policy if permitted or choose another way of solving the problem.
Example 2: Safeguarding sensitive data in documents
A team member tries to share a document containing personally identifiable information (PII) such as a social security number in a Teams channel. If the DLP policy includes SharePoint and OneDrive locations, it will prevent unauthorized users or external guests in that channel from accessing the shared document. Recipients will see a notification that the document is blocked due to a policy violation.
Example 3: Enabling safe communication in Teams shared channels with external users
Organization A collaborates on a project through a Teams shared channel with Organization B. When an employee attempts to share financial data in the channel, Organization A’s DLP policy enforces a block on the message so that sensitive information is not inadvertently shared with external users from Organization B.
These examples illustrate how continuous monitoring of Teams data alerts to different triggers, which facilitates the appropriate actions to safeguard the data and notify users to the policy rule in question. This proactive approach doesn’t wait until the data is compromised but rather prevents the leak and keeps the Teams environment secure.

Research: The True Scale of Risk in Collaboration Data
DLP reporting on Microsoft Teams
Microsoft Purview provides comprehensive reporting capabilities, giving admins the ability to monitor activity and manage reports and alerts related to DLP policies.
To access DLP reports
- Navigate to the Microsoft Purview compliance portal.
- Go to the “Data Loss Prevention” section.
- Select the “Activity Explorer” tab to access DLP reports. These reports contain detailed information about DLP activities, including:
- Files with sensitive information and their types.
- Data exfiltration activities and attempts.
- DLP policies and rules that detected activities.
- User overrides of DLP policies.
- Actions taken by DLP policies (e.g., blocking, encrypting, etc.).
You can filter the reports by criteria, such as date range, location, activity type, etc., to narrow the results and focus on areas of interest.
Activity Explorer section
In Microsoft Purview, the Activity Explorer section provides a centralized view of the DLP policy activities across Microsoft 365, including Microsoft Teams. Admins can:
- View the last 30 days of DLP information through preconfigured filters for endpoint DLP activities, files containing sensitive information types, egress activities (data exfiltration attempts), and more.
- Customize filters to analyze specific DLP events.
- Identify users who have overridden DLP policies and the justifications for doing so.
- Monitor DLP rule matches and actions the policies have taken.
Monitoring alerts in the alerts dashboard
- In the Microsoft Purview compliance portal, go to the “Alerts” section under the “Data Loss Prevention” tab.
- The alerts dashboard displays all the DLP alerts, including those related to Microsoft Teams.
- You can triage alerts, set investigation status, and track resolutions from the dashboard.
- Alerts can also be seen in the Microsoft Defender portal, which makes additional investigation tasks available.
These three locations provide admins the accessibility they need to monitor policy activities and violations, take action, and protect sensitive data from within Microsoft Teams and throughout the organization’s ecosystem.
Integrate with Aware for advanced AI-powered DLP
Admins often find that the out-of-the-box solutions provided by tools like Microsoft Teams don’t fully cover their needs when it comes to creating a robust DLP policy. For example, you need an Enterprise 3 subscription just to get the basic DLP capabilities for Exchange Online, SharePoint Online, OneDrive for Business, and Microsoft Teams. For any kind of customizability and advanced integration features, you’ll need an E5 subscription.
Aware was purpose-built to protect data assets against unauthorized access and sharing. Designed with data handling and security in mind, Aware’s features:
- Help you set granular rules and DLP policies for robust data protection.
- Use natural language processing and AI machine learning to understand events at human accuracy levels, which returns fewer false positives in alerts.
- Preserve the context surrounding a violation so you can understand the reason why sensitive data was shared.
- Automatically address violations with real-time coaching of employees.
- Use role-based access controls (RBAC) to define authorization and limit data exposure.
- Consolidate DLP management across all your collaboration tools, not just Teams, from a secure, centralized platform.
Aware helps the world’s leading organizations reduce data loss, gain visibility on where their data is and who controls it at all times, including a large utility company that after a recent acquisition was concerned about employees sharing sensitive trademarked data across internal collaboration channels. With Aware, they were able to surface data-sharing instances, flag them, and block them with appropriate DLP rules that allowed them to maintain compliance in their regulated industry.
Are you ready to build a robust DLP policy for Microsoft Teams? Request a demo today!