AWARE FOR dlp
Protect against data exfiltration from collaboration tools
Protect sensitive data from leaks and reduce shadow IT with a platform purpose-built to identify unauthorized access and exfiltration attempts.
About enterprise dlp
What is DLP?
DLP (data leak prevention/data loss protection) is a set of tools and processes that organizations use to protect sensitive information from unauthorized access or exfiltration. By monitoring data flows and applying security measures, DLP safeguards confidential information like financial records, customer data, and intellectual property, ensuring it stays in the right hands.
DLP solutions employ a combination of techniques to monitor and track data movement across the enterprise and automate remediation, including content inspections, contextual analysis, and policy enforcement workflows. Collectively, these measures can help mitigate the loss of sensitive data due to negligence or malicious actors.
IMPORTANCE OF DLP
Why you need data exfiltration protection for collaboration
Collaboration tools like Slack and Microsoft Teams generate one of the largest and fastest-growing datasets in the modern enterprise, making DLP essential to close the loop on protecting all company-owned data.
Protect your company’s most valuable data
DLP policies that detect and remediate multiple kinds of sensitive data, including PII, PCI, PHI, and intellectual property, help safeguard sensitive information and ensure it remains secure.
Secure your digital workplace
DLP extends data protection to digital environments like Slack and Teams, ensuring that sensitive information remains safe in cloud-based collaboration and storage solutions.
Improve regulatory compliance posture
Many regulations like GDPR and HIPAA require organizations to implement data protection measures. DLP helps ensure compliance, avoiding hefty fines and legal repercussions.
Detect and prevent insider threats
People are the new threat vectors, and collaboration tools can provide cover for both malicious and negligent actors, increasing the risk of insider threats. DLP mitigates this risk by monitoring the actions of employees and authorized users.
Gain contextual oversight of your organization
Go beyond tracking data movement to understand how information flows throughout the organization to limit shadow IT, improve workflows, and enhance productivity.
Identify weaknesses in systems and apps
DLP controls can help identify the weak spots where data is at risk, helping to strengthen the organization's risk posture.
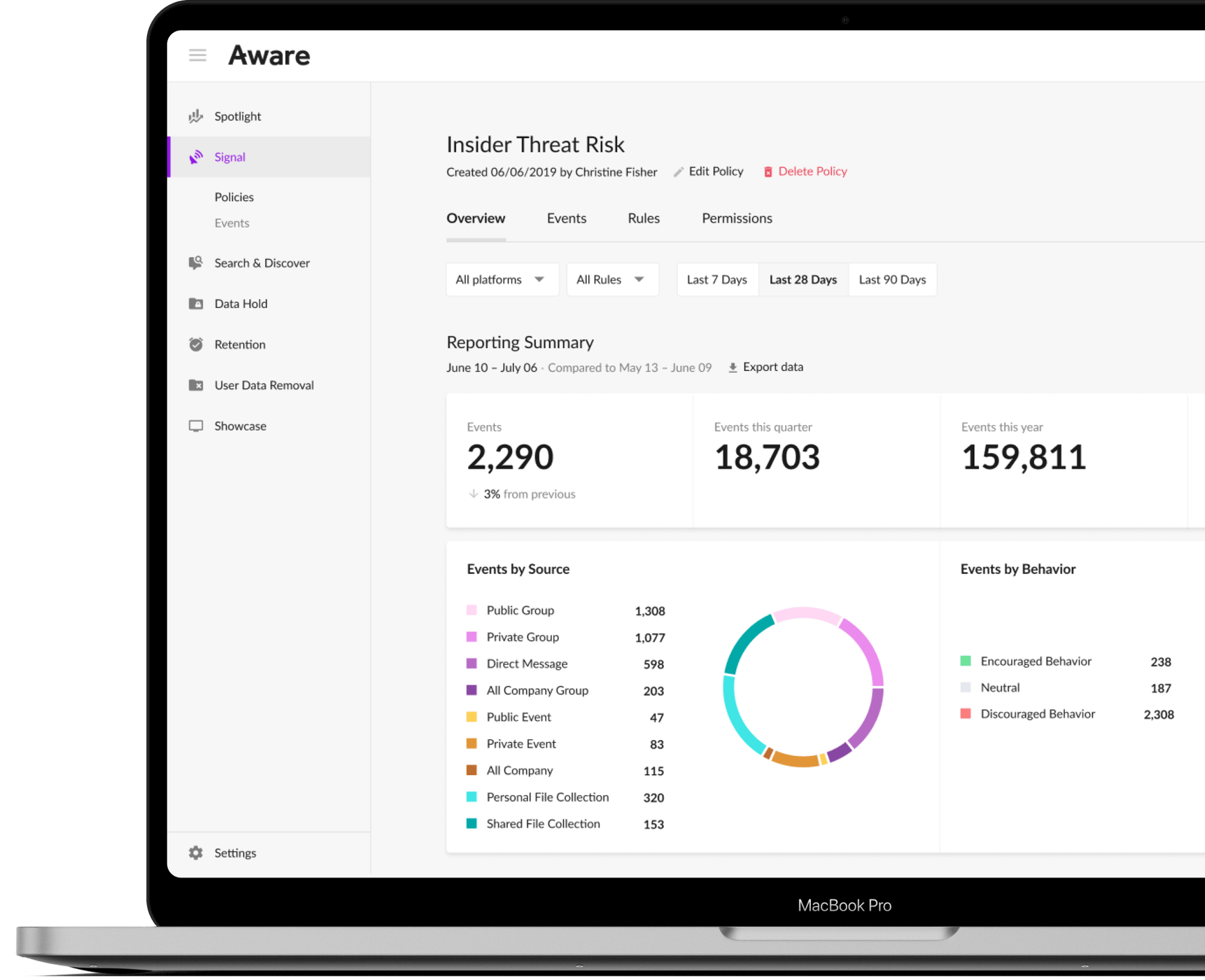
Aware capabilities
Reduce the complexity behind DLP with Aware
Identify unauthorized data access, exfiltration attempts, and malicious behaviors faster and more effectively.
Design rules tailored to your business’s unique needs
Flexibly create custom policies and rules that can apply across various platforms, channels, users, file types, messages and images.
Utilize the industry’s most accurate AI-powered detection
Reduce false positives with Aware’s proprietary ML models that detect images, screenshots, code, passwords and PII with human-level accuracy.
Empower your team and respond to incidents in an instant
Automated actions notify team members, educate content authors, hide or directly remove data from platforms.
Understand the why behind behaviors
Context-rich alerts and reporting provide insight into potential data exfiltration, insider threats or accidental blind spots.
Merge with your existing workflows
Access alerts from your collaboration platforms, the Aware dashboard, or use Aware’s API to connect to your SIEM.
Maintain complete control and visibility over company data
Security features include role-based access and message visibility controls.
Learn more

5 Reasons Why You Need DLP for Slack
Every business should outline acceptable and unacceptable use policies, but when it comes to collaboration tools the rules may become blurred.

Complete Guide to Data Loss Prevention (DLP) in Google Workspace
Data is one of your organization’s greatest assets and biggest liabilities.
Complete Guide to Data Loss Prevention (DLP) in Slack
Tools like Slack play a vital role in enabling collaborative work for businesses and organizations.
Questions? We're here to help
Everything you need to know about data loss prevention.
What are the benefits of DLP?
DLP, or data loss prevention, encompasses strategies to safeguard corporate information from unauthorized access. By employing effective tools and controls, organizations can ensure the secure management of their data, bolster data privacy, and minimize the likelihood of breaches.
In addition, DLP providers can:
-
Enhance compliance with regulations like HIPAA or GDPR by classifying and managing sensitive data efficiently, simplifying compliance audits.
-
Improve data visibility and provide insights into how data is used and transferred across the organization, allowing for better data governance and policy enforcement.
-
Mitigate insider threats by flagging suspicious activity, reducing the risk of intentional or accidental data leaks.
What are the main causes of data loss?
While there are 5 primary causes of data leakage, the most common is human error. Whether by falling for a phishing attack, using shadow IT to circumvent cybersecurity safeguards, or simply uploading the wrong file into a public Slack channel, simple mistakes and lapses of judgment are the cause of a major of data loss incidents. The other causes are:
-
Insider threats: Malicious employees or other authorized users who deliberately exfiltrate or compromise data
-
Cyberattacks: Hackers who target sensitive data by exploiting vulnerabilities in systems, deploying ransomware, or tricking users into sharing information
-
Hardware failures: Unsecured, misconfigured, or obsolete technology can create system malfunctions or crashes
-
Software vulnerabilities: Caused by anything from weak passwords and lack of two-factor authentication to encryption failures or unsecured integrations
What should you look for in a DLP solution?
When selecting DLP software, key considerations include data discovery capabilities, integration with existing IT infrastructure and cloud applications, and scalability to accommodate organizational growth. Additionally, a user-friendly interface, robust encryption options, and flexibility in defining and customizing security policies are essential factors to look for in a DLP solution.
For enhanced DLP functionality, security teams should consider solutions with granular data classification capabilities that can identify and protect different types of sensitive information, paired with automated enforcement and remediation capabilities such as blocking unauthorized data transfers, encrypting sensitive files, or alerting administrators. Many such functions are today available by partnering with an AI-powered data loss prevention software provider that uses machine learning technology to automate much of the work of identifying risky user behavior, classifying policy violations, and remediating risk in real time.
Types of sensitive information DLP tools should be able to identify include personally identifiable information (PII), credit card numbers and other PCI DSS data, and protected health information (PHI). Additionally, consider a data loss prevention solution with the functionality to identify critical data and intellectual property (IP).
DLP tools should also be able to monitor various data channels (email, endpoints, cloud storage, SaaS apps) and detect suspicious activity in near real time to minimize the risk from malicious actors. Finally, your DLP solution should produce comprehensive reports and audit logs for compliance and review.
What are best practices for data loss prevention?
An effective DLP strategy starts with a risk assessment to discover where sensitive data and potential threats exist within the organization’s corporate network. This can include endpoints such as laptops, routers, and personal devices in a BYOD environment and cloud services such as collaboration tools. Once weaknesses are identified, it’s important to implement clear and comprehensive security policies and compliance requirements, educating end users about data security. This can reduce instances of information risk, data theft, and shadow IT.
In tandem with DLP policies, admins should enforce acceptable use and conduct by regularly monitoring and auditing the access and usage of different types of data, encrypting sensitive information, keeping software and security systems up-to-date, and establishing incident response plans to address and mitigate enterprise data breaches promptly. Regular training and awareness programs for employees also contribute to a proactive and security-conscious organizational culture that puts information protection at the forefront of the digital workplace.