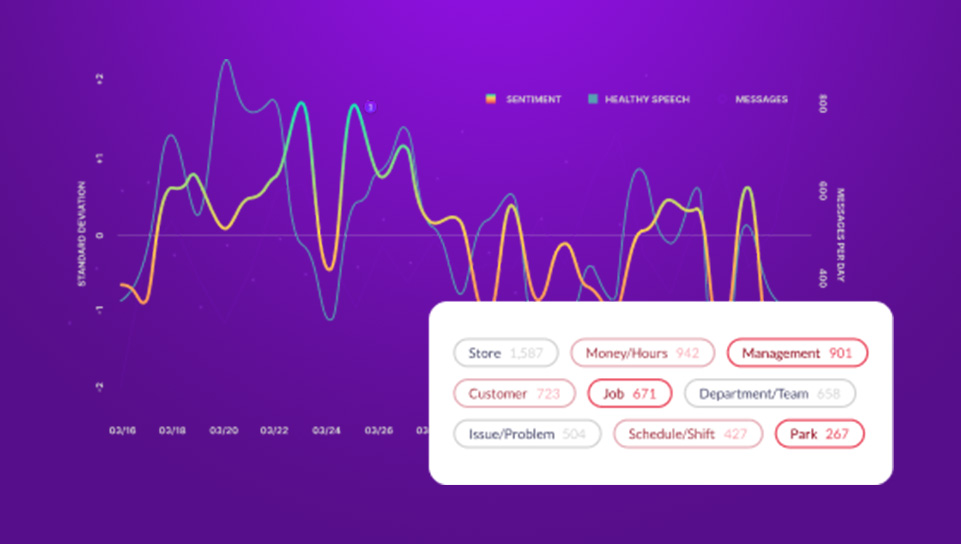
What Is a Data Loss Prevention Policy?
by Aware
Data loss prevention (DLP) policies are safeguards organizations establish to protect sensitive data from unauthorized access or data leaks. They’re intended to ensure the privacy and security of a company’s critical data assets, including intellectual property, customer information, financial records, or other proprietary information.
Contents
- What is a data loss prevention policy?
- What are the benefits of having a DLP policy?
- What are the steps to creating a comprehensive DLP policy?
- Best practices to consider when building your company’s DLP policy
- How Aware helps you implement and strengthen your DLP policy
What is a data loss prevention policy?
A DLP policy is a set of rules and guidelines designed to protect company-owned data during regular use. Such polices are the first vital step toward compliance with regulations and industry standards such as HIPAA, GDPR, PCI DSS, CCPA/CPRA, PIPEDA, and more. These rules are continuously updated, which must be reflected in an organization’s DLP policies.
What is data loss prevention?
DLP involves identifying and securing the movement of sensitive data within an organization’s network and on devices like desktops, laptops, and smartphones. Robust DLP policies actively curtail unauthorized sharing and exposure of sensitive data internally and externally.
The tools and solutions used to enforce DLP policies provide capabilities such as data access and classification, exfiltration detection, incident response, and DLP monitoring. Using DLP solutions, information security teams can take a centralized approach to enforcement and information protection.

Whitepaper: How to mitigate data risks in Slack
What are the benefits of having a DLP policy?
Improve data visibility
A comprehensive DLP policy provides visibility into sensitive data types, where data resides, and how it flows throughout the organization. This gives companies the best opportunity to classify, monitor, and control access to sensitive information.
Protect intellectual property and sensitive data
The number one purpose of a DLP policy is to protect critical data assets. This includes intellectual property, customer data, financial records, research, and other proprietary information. Few people know the recipe for Coca-Cola. Even things less renowned, such as hospital blueprints, or client mailing lists can still be indispensable to an organization. All of these are examples of the type of valuable and confidential data a DLP policy is designed to protect.
Compliance adherence
Regulatory compliance is frequently top-of-mind for infosec leaders in highly regulated industries like healthcare (HIPAA) and finance (SEC/FINRA), but most organizations have to comply with some retention and data protection rules, such as GDPR, PCI DSS, or SOX.
These regulations frequently update, so keeping employees apprised of changes through continuing education should be part of an effective DLP policy.
Lower the risk of fines for noncompliance and data breaches
Organizations implementing effective DLP policies have the benefit of reducing their risk of data breaches or mishandling information, which saves noncompliance fines and penalties as well as potential lawsuits. DLP policies also prevent the reputational damage associated with data leakage, which can also harm a company’s bottom line.
Control the flow of information and access to sensitive data
A comprehensive DLP policy gives companies granular control over the flow of sensitive data throughout their frameworks. The modern-day business uses a diverse ecosystem of endpoint devices, cloud environments, networks, and collaboration tools. Proper DLP policies define role-based access and permission for handling sensitive information in these tools and systems while enabling employees to work effectively.
Detect and monitor suspicious activity
The right DLP tools, guided by a robust DLP policy, can detect and monitor suspicious activities, such as unauthorized attempts to copy, share, or exfiltrate sensitive data. This proactive monitoring helps organizations surface and respond to potential data breaches or insider threats promptly to minimize damage and enact remediation.
Webinar: Your legal ops checklist for collaboration data
What are the steps to creating a comprehensive DLP policy?
The benefits of a good DLP policy seem clear-cut, but what makes a DLP policy strong? Reviewing the following when creating a DLP policy ensures your organization has considered most of the common angles of data protection. There may be additional steps to consider for tailoring your policy to your organization, but these are a great start.
Perform a data audit
Knowing where and how your data is stored is essential. Your first step should be to conduct a comprehensive data audit to:
- Identify the types of sensitive data your organization handles
- Understand where your data resides (cloud storage, databases, endpoints, etc.)
- Know who can access the data
You can accomplish this step with automated data classification tools or by consulting with department heads and stakeholders and asking some important questions about their data usage.
Identify what data needs to be protected
Once your data is audited, you can classify the data. Does any of it fall into categories that are protected by regulatory bodies or laws? Examples include PHI, PCI, and PII. These types of data should be highly prioritized for protection, and DLP monitoring and retention rules should comply with regulatory requirements. You should also consider what intellectual property is crucial to business operations and how your DLP policies can preserve it.
Identify what information requires archiving
Hand-in-hand with the previous step, establish guidelines for archiving and retaining data based on legal requirements, industry standards, regulations, and organizational policies. Some regulated records may need to be retained for a number of years before they can be purged. Implementing data preservation rules reduces the risk of unauthorized access or misuse while still maintaining compliance.
Create an action plan for the detection of suspicious activity
If unusual or anomalous activity raises an alert, which should trigger a series of mitigation procedures. Defining these procedures and actions ahead of time leads to the smooth handling of an when it happens. This may involve informing relevant personnel, blocking the activity, quarantining the data, or initiating incident response procedures.
Analyze data movement
There are different ways data moves through an organization. Understanding that movement can help with how the data is managed, and therefore how it’s protected.
- Data at rest—stored in databases, on file servers, or in cloud storage
- Data in use—data actively being processed or accessed by users or applications
- Data in transit—data being transferred over networks or between systems and applications
When you recognize where data is at all times, you can establish controls and monitoring mechanisms to safeguard it regardless of its location.
By implementing these steps, organizations can build an inclusive DLP policy that protects the data throughout its lifecycle. Identifying, classifying, monitoring, ensuring compliance, archiving, and responding to incidents are some of the most common steps a DLP policy should contain.

Whitepaper: 6 Critical data risks—and how to avoid them
Best practices to consider when building your company’s DLP policy
While the above steps are a great place to start, there may be other considerations to adapt your DLP policy to your organization. By being mindful of these best practices, you can ensure all-inclusive data protection with your DLP policy.
Determine the most important objectives
While forming your DLP policy, ask yourself what primary objective you want to achieve. Are you most concerned about preventing data breaches? Is regulatory compliance a bigger priority? Or is your intellectual property’s security key? This answer will guide your policy’s scope and resource allocation.
Ensure stakeholder participation across all relevant departments
The stakeholders from IT, legal, HR, and other business units that handle sensitive data must be involved. They will have valuable input, and their buy-in is crucial for creating a comprehensive and practical DLP policy that addresses the data’s diverse protection needs. The organization will be better off having these team members’ approval of the DLP policy.
Establish evaluation criteria for DLP solutions
What are your needs versus luxuries your DLP software solutions must have? Things such as operating system compatibility, deployment options (on-premises or cloud), scalability, and integration with existing platforms and security tools are factors to consider.
Define stakeholder roles and responsibilities
The roles of stakeholders involved in implementing, maintaining, and enforcing the DLP policy should be clearly outlined. Data owners, security teams, IT administrators, and end users should all know the parameters of their duties for accountability to and compliant execution of the DLP policy.
Train employees on the DLP policy
Regularly training employees and offering awareness programs to educate your workforce about the DLP policy, its importance, and their responsibilities in protecting sensitive data makes them feel like part of the solution. Emphasize best practices and potential risks, and ensure they understand the consequences of noncompliance.
Create KPIs to measure DLP efficiency
Providing key performance indicators to measure the effectiveness of your DLP strategy (e.g., the number of incidents detected, incident response time, false positive percentage) can help improve your data protection posture. Reviewing these metrics will identify areas for adjustment to the policy and closing the gaps.
Following these best practices helps organizations customize their DLP policies to adapt to their priorities, develop robust DLP solutions, meet regulatory requirements, and align with specific business needs and risk profiles.

Download: Align legal & IT on collaboration security
How Aware helps you implement and strengthen your DLP policy
Having a purpose-built platform such as Aware underpinning your DLP policy makes protecting your data assets against unauthorized access and data mishandling easier than ever. Aware reduces the complexity of DLP to detect and address data security incidents without blocking collaboration and the flow of business.
With Aware’s DLP solutions, you can:
- Build strong DLP policies with flexible rules that apply to multiple collaboration tools, data and file types, users, and storage locations to cover your organization’s unique needs.
- Empower your people to protect your organization’s data assets with automated actions that alert IT teams, quarantine data, block suspicious activity, and educate content authors on incidents in an instant.
- Reduce false positives with the industry’s most accurate NLP and machine learning models that detects code, passwords, PII, screenshots, images, and more with human-level accuracy.
- Gather understanding around behaviors with reporting insights that provide context-rich alerts for insider threats, accidental data mismanagement, and potential data exfiltration.
- Gain complete visibility and control over company data with security features that include role-based access controls.
At Aware, we’ve helped companies large and small protect their data wherever employees collaborate.
For one large technology service company, Aware gave them the tools they needed to secure intellectual property when consultants and contractors worked on highly sensitive projects with their own mobile devices. Aware’s features ensured all data shared was appropriate and safe for the situation and context provided.
Are you ready to develop your DLP policy and protect your most valuable data assets? Request a demo today!