5 Slack Data Breaches You Should Know About
by Aware
Slack is a popular collaboration tool in many workplaces, including 77% of the Fortune 100. However, this popularity introduces risk. Today’s hackers know that Slack is a valuable repository of sensitive, confidential, and proprietary data—everything from company financial records, product roadmaps, customer lists, sales plays and more can be found in Slack, and that makes this data set a top target of threat actors. Here’s 5 times that Slack accounts have been hacked or breached, and what you need to know to protect Slack from hackers at your organization.

What risks live in Slack? We analyzed 6.6B real messages to find out.
Contents
- Slack Data Breach 1: Disney
- Slack Data Breach 2: Uber
- Slack Data Breach 3: Grand Theft Auto
- Slack Data Breach 4: EA Games
- Slack Data Breach 5: Twitter
- Bonus: How Slack was almost hacked
- How to protect Slack from hackers
- How Aware supports data security in Slack
Slack Data Breach 1: Disney
Disney is the latest high-profile victim of Slack hackers, after hacktivist group Nullbulge targeted the entertainment giant "due to how it handles artist contracts, its approach to AI, and it’s [sic] pretty blatant disregard for the consumer."
What happened?
In July 2024, Nullbulge released 1.1TB of Disney's Slack data, dating back to 2019, from "almost 10,000 channels, [including] every message and file possible." The group claim to have been given access to the company Slack by a Disney insider—who they then named in retaliation after he allegedly withdrew that access.
Contained within the published data were passwords, APIs and other login credentials, code, and details and images from unreleased projects.
What was the outcome?
While the original data dump was taken down, it is still being widely shared on mirror sites. Disney itself has remained tight-lipped about the hack, simply saying in a statement to the Wall Street Journal that they are investigating the incident.
What's in your Slack data? Use Aware's free online calculator to find out now.
Slack Data Breach 2: Uber
In September 2022, a user took to Uber’s #General Slack channel to announce that they had hacked the company’s systems. Initially, employees assumed the message was a joke, but it quickly became apparent that a real data breach had taken place.
What happened?
The likely source of the hack was an Uber contractor’s phone that was infected with malware. Credentials from the phone were exfiltrated and sold on the dark web to the hacker, later identified as Arion Kurtaj, 18. Kurtaj used a simple multi-factor fatigue attack to bombard the contractor with login requests until one was finally approved. From there, Kurtaj was able to access a number of Uber’s systems in addition to Slack, including Google Workspace, AWS, OneLogin and HackerOne.
What was the outcome?
The prosecution of Kurtaj revealed Uber suffered almost $3 million in damages as a result of the hack. To remediate the breach, Uber was forced to block employee access to internal systems, disable critical internal tools, and lock down its codebase until a full analysis of the situation was completed. Going forward, Uber invested in additional monitoring solutions to support its threat-hunting initiatives.
Read more: The Uber breach demonstrates why we built Aware
Slack Data Breach 2: Grand Theft Auto
The same hacker responsible for the Uber data breach struck again just days later, breaching Rockstar Games’ Slack instance and exfiltrating footage of their highly anticipated upcoming game, Grand Theft Auto VI.
What happened?
While the exact mechanism of the Rockstar Games hack is unknown, it is likely that Kurtaj used similar social engineering techniques to gain access to the company Slack. From there, he found and exfiltrated 90 videos of game footage and posted them to the fan site GTAForums.
Kurtaj also claimed to have downloaded the source code for both Grand Theft Auto VI and GTA5 and responded to reports the claim was bogus by posting snippets of GTA5 code that appeared authentic.
What was the outcome?
Rockstar Games said that recovering from the hack cost $5 million plus “thousands” of man-hours. For these and other cybercrimes, Kurtaj was sentenced to be held indefinitely at a secure medical facility until doctors could be satisfied he was “no longer a danger.” A 17-year-old co-defendant received an 18-month rehabilitation order.

Slack data risks: Stats and facts you need to know
Slack Data Breach 3: EA Games
Another high-profile gaming hack occurred in June 2021, when an employee at Electric Arts was tricked into providing a login token over Slack. Once inside EA’s systems, the hackers exfiltrated source code for FIFA 21 and the Frostbite engine that powers many of EA’s games.
What happened?
The hackers claim to have gained access to Slack by purchasing stolen cookies—small pieces of text that can contain login information about web users. It had been reported a year earlier that a former EA engineer accidentally exposed internal Slack channel names on GitHub, as well as credentials for EA’s infrastructure monitoring software where Slack login tokens were configured, potentially aiding the hackers in accessing and navigating EA’s internal systems.
What was the outcome?
The hackers claimed to be in possession of 780GB of EA source code and other critical data, which they offered for sale for $28 million. When they failed to find a buyer, they attempted to extort EA by threatening to post all the data publicly if they did not receive a ransom payment for its return. In July 2021, after EA refused to pay, the hackers released the entire cache on a cybercrime forum.

Get your copy of the full report to discover your real risk exposure in Slack
Slack Data Breach 4: Twitter
In July 2020, over 130 high-profile Twitter accounts were targets of a simultaneous hack that saw them tweeting out links to a crypto scam in a hack that was eventually traced back to Twitter’s Slack instance.
What happened?
According to an investigation by the New York Times, hackers infiltrated Twitter’s Slack account using social engineering, and there found credentials to Twitter’s backend systems. Using those credentials, they were able to take control of any Twitter account. As well as using the accounts to tweet malicious links, they downloaded data from eight Twitter users.
What was the outcome?
The hack took Twitter several days to contain, and the company was forced to take extreme measures, including disabling tweeting for verified accounts and locking millions of users out of Twitter. Three people were later arrested and two received custodial sentences of three and five years. At the time of the breach the hackers claimed to have made 20 Bitcoin from the scam, worth approximately $180,000. Twitter’s stock price fell 4% and the company was forced to delay the rollout of its new API in the aftermath.

Whitepaper: Risk Management in Slack
Bonus: How Slack was almost hacked
In March 2020, Slack announced it had patched a security flaw that enabled automated account takeover attacks, which unchecked could have led to significant data breaches.
What happened?
In November 2019, a researcher discovered a way that hackers could access Slack user cookies through HTTP requests. This gave hackers a way to hijack active Slack sessions and access almost any Slack instance. Compounding the risk, the hack method was one that could be automated, meaning threat actors could quickly target thousands of victims.
What was the outcome?
The researcher reported the weakness to Slack via their bug bounty program, giving Slack the opportunity to resolve the issue before any accounts were compromised. To date, Slack has paid out over $1.9 million to researcher who have identified vulnerabilities in its software.

Mitigate data risks in Slack. Download the whitepaper now.
How to protect Slack from hackers
Organizations can protect their Slack data and mitigate the risk of a hack or breach using many of Slack’s native security and privacy controls. Some options available to Slack admins include two-factor authentication (2FA), SAML-based single sign-on (SSO), enterprise key management (EKM), and IP whitelisting, although a full list of capabilities depends on the Slack account tier. Slack also protects the data it holds through compliance with industry standards such as SOC 2 Type II and ISO/IEC 27001, and through its bug bounty program, which helps to identify and mitigate software vulnerabilities before threat actors find them.
Learn more about how to secure your organization’s Slack
Configuring a Slack instance for data privacy and protection is only one aspect of mitigating risk. As these high-profile Slack data breaches show, sometimes the weakest link in your organization is your people. Social engineering and MFA fatigue attacks are common ways that malicious actors can infiltrate a Slack workspace and become insider threats.
How Aware supports data security in Slack
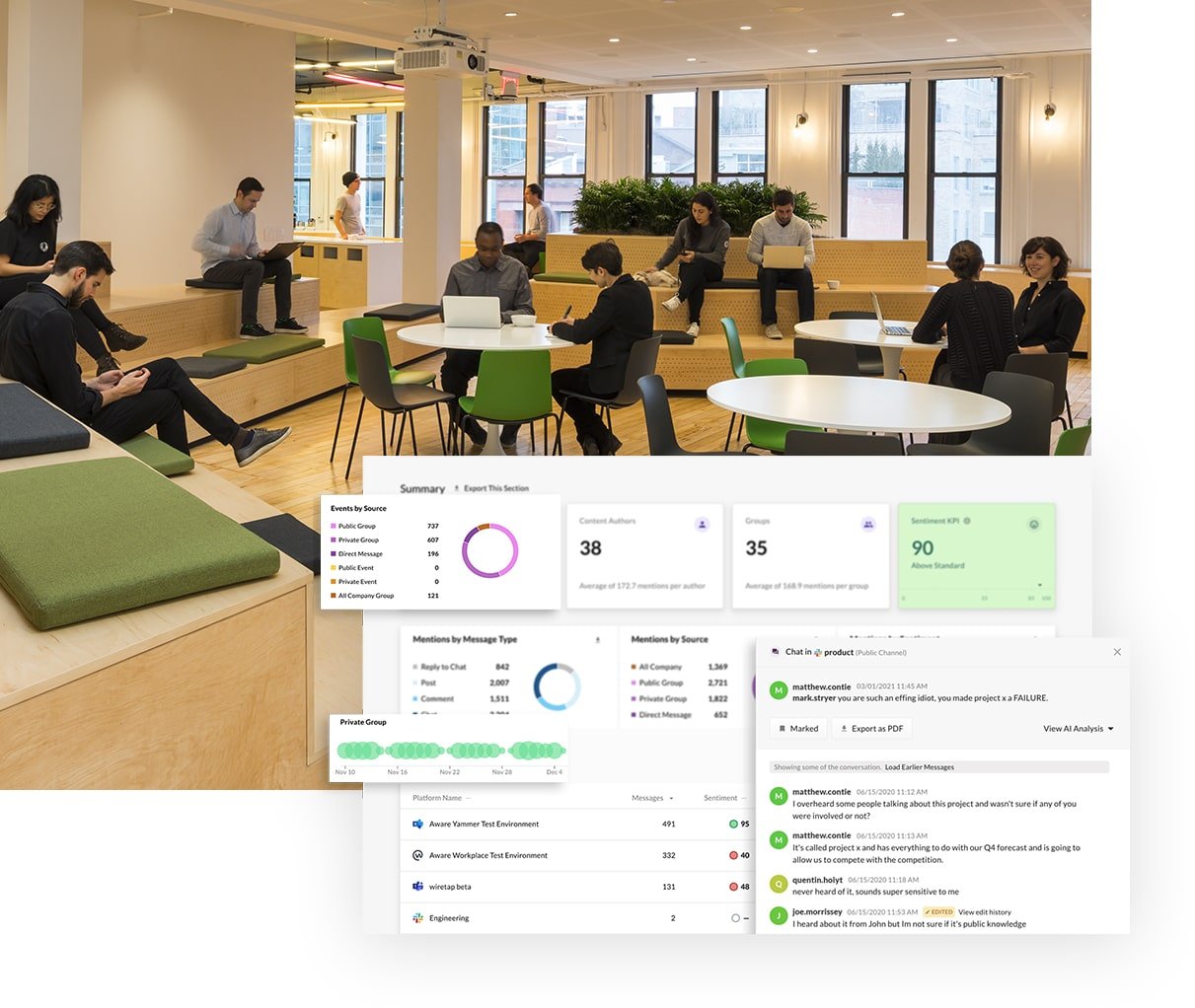
Aware is the only Slack vendor approved for both data loss prevention (DLP) and eDiscovery. Aware connects natively to Slack via API and ingests and analyzes Slack messages in real time using proprietary NLP and AI/ML models that detect sensitive information and unauthorized activity in real time.
Using Aware, organizations can take control of their Slack instance with granular rules configured to their workspace’s unique environment and detect and mitigate more instances of data risk with fewer false positives.
- Identify multiple types of sensitive data using keywords and regex, including PII/PCI/PHI and IP
- Apply granular rules to employee groups or channels to contain Slack data and limit visibility
- Create bidirectional retention settings to purge or preserve data according to regulatory need
- Perform fast, federated search across the entire Slack workspace and refine by multiple parameters
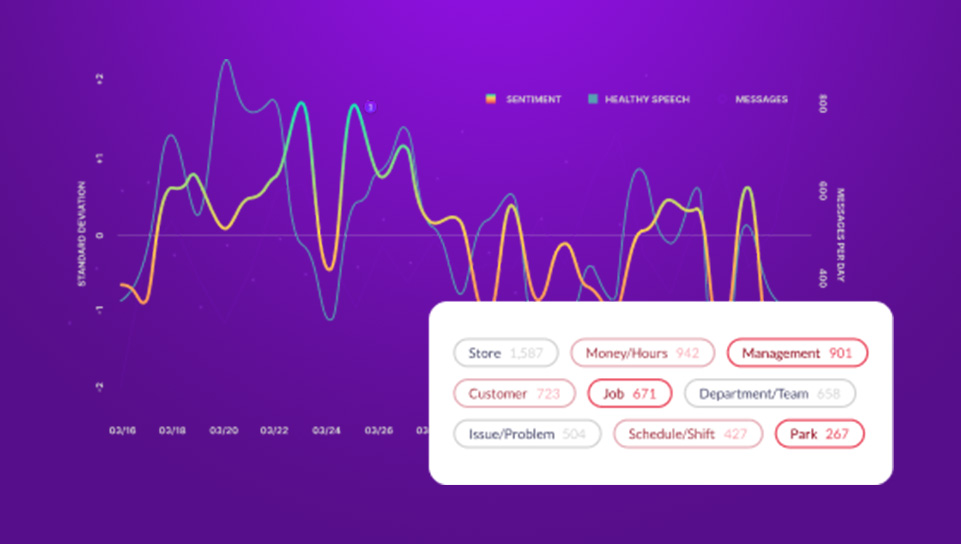
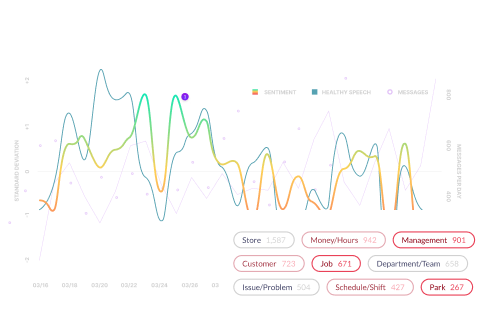
- Leverage industry-leading sentiment analysis NLP to detect behavior anomalies as they occur
Aware is backed by enterprise-grade security and privacy controls and is GovSlack compatible for use by government agencies and partner organizations.