Understanding and Tackling Slack Insider Threats: How to Monitor, Identify, and Mitigate
by Aware
Insider risk places a unique burden on information security officers because the threat actors exist behind the secure perimeter that shields confidential and sensitive data from outsiders. While threat-hunting internally is always a challenge, collaboration tools like Slack provide surface areas where insider threats can act unseen.
Aware Future of Work Research Series
We analyzed billions of real employee chats and found — among other insights — that confidential information is shared in 1:166 Slack messages.
In this blog post, we'll dive into the realm of Slack insider threats, exploring their origins, types, and most importantly, strategies to prevent and manage them effectively.
Contents
- What are Slack insider threats?
- Where do Slack insider threats come from?
- 3 types of Slack insider threats
- Why is Slack a risk for businesses?
- Cloud security in Slack
- How increased adoption of Slack leaves organizations exposed
- Preventing, mitigating, and managing Slack insider threats
- Insider threat mitigation for Slack from Aware
What are Slack insider threats?
Insider threats in Slack are internal actors who, through malice of mistake, pose a risk to the organization by misusing their access to the platform for harmful purposes. These threats can lead to data breaches, leaks of sensitive information, reputational damage, and other serious consequences for businesses if they are not proactively addressed and quickly mitigated.
Where do Slack insider threats come from?
These threats can arise from various sources within an organization. While some might be unintentional, others are deliberate and malicious. It's essential to understand the origins of these threats to build a comprehensive defense strategy.
3 types of Slack insider threats
Slack insider threats typically fall into three types: inadvertent actors, malicious insiders, or outsiders. Each type of threat actor has different motivation and can do varying amounts of damage to an enterprise. An inadvertent actor could leak the IP of your company’s top-secret project and create a crisis but could just as likely share far less valuable information. Meanwhile, malicious actors will deliberately target the most valuable information they can find, making them a top priority to identify and mitigate.
Inadvertent ActorsOften, insider threats are not born out of malice, but from mistakes. Employees might accidentally share confidential information in the wrong channel or attach sensitive files to a public conversation, inadvertently exposing crucial data.
Data shows that around a quarter of insider threat incidents are triggered by inadvertent actors. Your workers are simply trying to do their jobs and don’t always understand the risks associated with sharing sensitive information, documents, or passwords through Slack, or why those behaviors create vulnerabilities for the organization.
OutsidersWhile Slack is designed for internal communication, external partners and contractors can also gain access using Slack Connect. If their permissions aren't adequately managed, they could unintentionally access sensitive information or even intentionally misuse it.
Outside actors account for almost half of insider threat incidents, making this by far the most common type of insider incident. It’s therefore essential for businesses to carefully vet contractors and vendors, and immediately revoke Slack access to any third-party once a business relationship ends.
Malicious InsidersPerhaps the most concerning type of threat actor, malicious insiders are individuals who intentionally exploit their access to Slack for personal gain or to harm the organization. This could involve leaking confidential data, intentionally spreading misinformation, or disrupting operations.
Think about everything that exists within your Slack data right now—business plans, financial projections, sales and marketing playbooks, and a wealth of interpersonal communication that could be embarrassing if it became public. Malicious actors account for around a third of all insider threats and could be active in your Slack channels right now.
Why is Slack a risk for businesses?
The convenience of Slack comes at a cost. As organizations become increasingly reliant on this platform, they expose themselves to potential vulnerabilities that could have far-reaching consequences.
Sensitive Information
Employees feel safe sharing sensitive information in work-sanctioned tools, and Aware research into Slack threats shows that the platform is packed with proprietary, confidential, and regulated information. In the wrong hands, this information could be devastating.
Just 1000 employees will send 435,000+ Slack messages each month. On average, those messages will contain:
- 87 passwords
- 10,000 screenshots
- 45 credit card numbers
- 2600+ pieces of business-sensitive information
Business leaders cannot ignore the risks associated with this kind of information sharing. Regulatory fines, reputational damage, and reduced competitive advantage can all result from Slack data breaches, impacting growth and profitability for the enterprise.
External Audiences
Guest users and Slack Connect channels both provide opportunity for people outside the enterprise to access the valuable information that Slack contains. While both types of users have restrictions placed on the channels they can access within the Slack workspace, if those channels are misconfigured or regular business users share sensitive information within them, that data will be fully available to the third-party members.
Because this type of user is the most likely to represent an insider threat to the enterprise, it is essential that they are admitted into the Slack environment only when truly necessary, and adequate precautions must be taken to safeguard information from accidental access.
Reputational Damage
While information such as payment card industry (PCI) data, personally identifying information (PII) and protected health information (PHI) are governed by various laws and industry regulations, not all sensitive information that Slack contains is so clearly defined. The way your employees behave within Slack—the language they use and how they interact—could also be damaging if it became public, eroding customer trust and investor confidence.
One workplace study found that 38% of employees reported experiencing harassment in the digital office, and 24% said that the harassment increased in remote tools like Slack. Scientists have long known that the anonymity of online interactions can increase rude, aggressive, and abusive behaviors. Given the limited visibility that admins have into what is said in Slack DMs and private groups, the risk of HR policy violations is high.
Workplace Incidents
There are many reasons a business may need to conduct eDiscovery or forensic investigation in Slack, but successfully responding to a workplace incident requires a proactive approach to managing and preserving Slack data. By default, Slack users (or “custodians”) retain full control over the messages they create. At any point, a user can edit or delete any message they send. That means it’s easy for a malicious actor to send a harassing message or exfiltrate data and delete all the evidence within moments.
Administrators must consider how they will handle internal conflicts, facilitate investigations, and secure Slack data for discovery—and do so before the need arises—to prevent spoilation of evidence or loss of context.
-min.png)
eDiscovery for Slack: Make sense of your JSON exports with Aware
Cloud security in Slack
As a cloud-based SaaS application, Slack security measures should account for how data is stored, accessed, and transmitted. Slack data is encrypted in transit and at rest for all Slack accounts and plans. Business, Slack Enterprise Grid, and GovSlack users have additional security options available to them, including Slack Enterprise Key Management (Slack EKM).
While Slack has yet to introduce end-to-end encryption, there are a number of cloud access security brokers (CASBs) available within the Slack App Store that can limit access to the workspace. By implementing measures to prevent Slack messages from being intercepted, organizations can strengthen their cloud security posture in Slack.
How increased adoption of Slack leaves organizations exposed
As Slack adoption grows, so do the opportunities for insider threats to strike. Over a year, just 5000 employees will send in excess of 30 million Slack messages. Even if only the tiniest fraction contain compromising, sensitive, regulated, or noncompliant information, that’s still a significant risk surface area—hidden among a mountain of innocuous messages that make discovery and containment infinitely more complex.
To put these threats into perspective, consider these real-life examples:
- The Uber Data Breach: Began with a multi-factor authentication (MFA) fatigue attack that granted a hacker access to several of Uber’s internal systems and accounts. From there, the hacker deliberately targeted Slack data for exfiltration before announcing the breach in a companywide Slack channel.
- Activision/Call of Duty: A hacker used social engineering to overcome 2-factor authentication (2FA) and enter the Slack environment of video game publisher Activision. Once inside, the hacker took screenshots of confidential working documents related to the latest Call of Duty game.
- Rockstar Games/Grand Theft Auto: Another game developer fell victim to a Slack cyberattack using an MFA fatigue attack. Once inside Slack, the malicious actor exfiltrated over 90 videos of the upcoming Grand Theft Auto VI game and posted them on a public forum, leaking critical characters, plot points, weapons and more.
Preventing, mitigating, and managing Slack insider threats
The most effective approach to counter Slack insider threats is the implementation of a comprehensive insider threat program that spans three key categories: people, processes, and technology.
People
Cybersecurity and Policy Awareness Training: Prevention is the enterprise's best form of defense. Employees should undergo training in spotting common risks like phishing and malware and know what to do when they encounter potential cybersecurity threats. In addition, regular training can educate employees about the risks of Slack usage, how to reduce company exposure by being mindful of the information they share, and proactively limit the available data that a malicious insider can intercept.
Processes
User and Entity Behavior Analytics (UEBA): By monitoring user behavior patterns, organizations can detect anomalies that might indicate insider threats in real time. The faster an insider threat actor is detected, the greater the opportunity to limit the damage. In 2020, Marriott Hotels was fined £18.4 million ($23 million) for failing to identify and mitigate an insider threat actor who exfiltrated sensitive data over a period of four years.
Secure Offboarding Procedures: Properly managing employee departures ensures their access to Slack and other platforms is revoked, minimizing the risk of unauthorized access.
Technology
Third-Party Apps: When integrating third-party applications with a Slack workspace, consider what information that app can access. Unsecured applications can open back doors into secure environments through which malicious actors can exfiltrate sensitive or compromising data. When you do use third-party integrations, ensure they are always kept up to date with the latest security patches.
Collaboration Intelligence AI: The Aware data platform integrates seamlessly with Slack and leverages proprietary AI and machine learning to identify unusual patterns and potentially malicious activities, providing an additional layer of protection against insider threats. Using Aware, businesses can deploy automations to consolidate, enrich, and uncover insights from digital conversation data at scale.
Insider threat mitigation for Slack from Aware
Using Aware, the world’s leading companies take a proactive approach to insider threat management, powered by industry-leading natural language processing (NLP) capabilities and intelligent AI analysis. Aware connects effortlessly to Slack workspaces using native APIs and ingests a full record of all Slack messages in real time, including edits and deletions, preserving a complete record of collaboration in an immutable archive that makes it faster and easier for businesses to conduct eDiscovery and forensic investigations into reports of a Slack insider threat.
Aware further enriches each message with complex AI and machine learning metadata that supports the detection of regular expressions (regex) and keywords. Then automated workflows apply Boolean logic to enhance the detection of regulated, restricted, and noncompliant information sharing within Slack and take immediate action to remove unauthorized content, coach employees, and notify leadership.
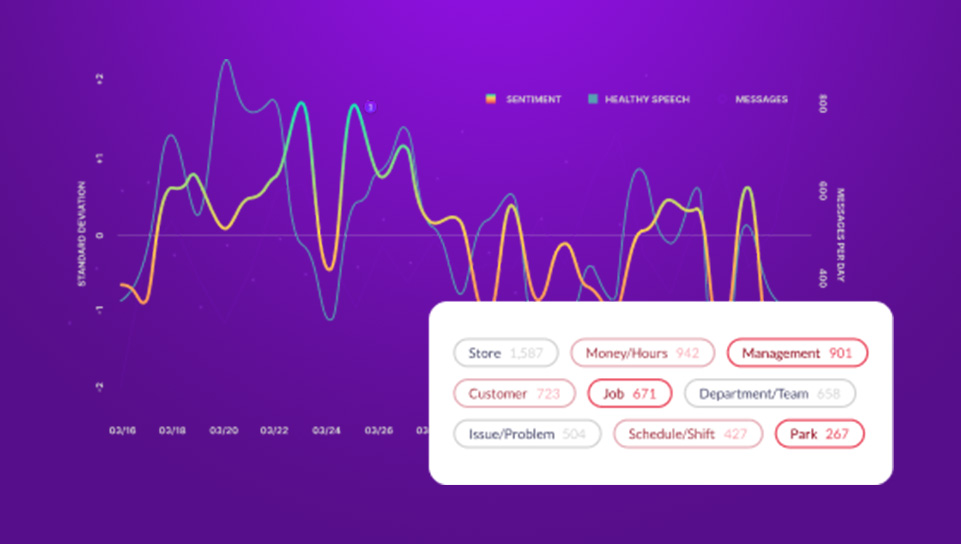
In addition to its powerful compliance and discovery tools, Aware also provides best-in-class sentiment analysis that outperforms all other leading competitors and delivers results at a near-human benchmark for the most accurate behavior analytics available today. Using these analytics, business leaders can visualize at-a-glance when activity within their Slack environment strays from acceptable parameters normalized for their unique digital DNA, proving a powerful early warning system that alerts to unusual activity within Slack.
Aware helps organizations to remain vigilant in detecting insider threats in Slack and address the unique risks presented by the Slack platform. With Aware, leaders are empowered to maximize Slack’s potential to accelerate work and enhance collaboration, while mitigating the risks associated with that data falling into the wrong hands.