Slack Security: How Well Is Your Sensitive Data Protected?
by Aware
First Published Feb. 2023. Updated Aug. 2024.
Slack offers many native security features that businesses can use to protect their data and their users. However, making the most of these features often requires advanced configuration and Slack Enterprise Grid. Even then, gaps can still remain, particularly for organizations covered by regulations such as HIPAA or GDPR. This post breaks down Slack security features and risks and explores how you can implement enterprise-grade security in Slack.
Is Slack Secure — Table of Contents
- Is Slack secure?
- What data does Slack house?
- Types of sensitive data shared on Slack
- What industries need to be particularly careful with Slack for security reasons?
- What are Slack’s in-built features?
- What are the different security concerns with Slack?
- Best practices for improving Slack security
- How Aware strengthens Slack security to safeguard your data
Is Slack secure?
As an enterprise collaboration tool, employees can be forgiven for assuming anything they type into Slack is protected and secure. Slack does provide a number of data security measures that shield user information from exfiltration. However, these measures may not be as comprehensive as users first assume, and many require Slack admins to proactively set them up.

5 high-profile Slack data breaches every company should know about
What data does Slack house?
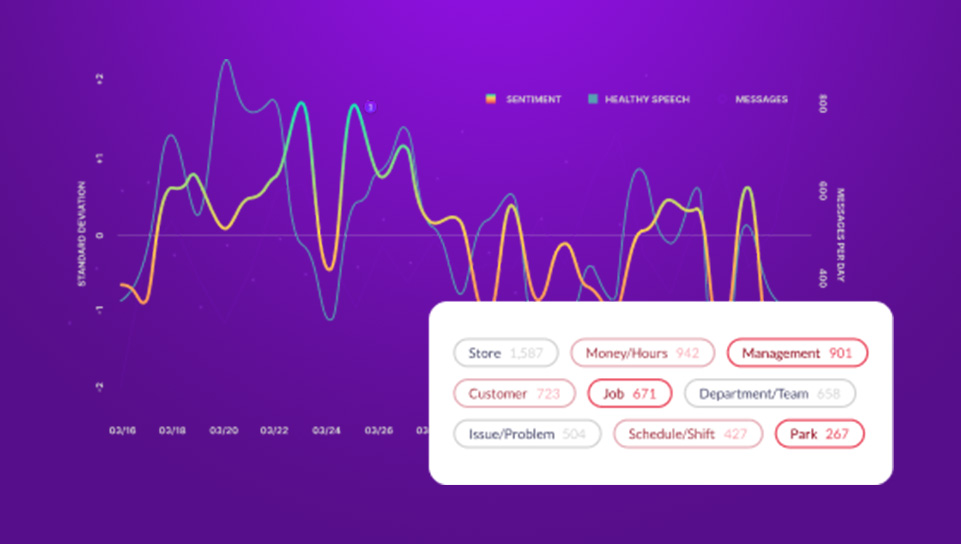
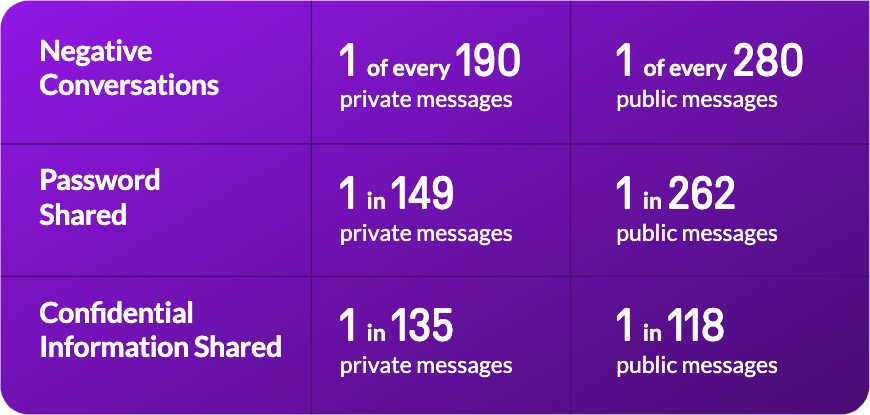
Aware insights from analyzing millions of real Slack messages paints a worrying picture. Our research shows that the average Slack environment is a tangled mess of blind spots, hidden risks and sensitive data.
Aware research shows that 1:166 Slack messages contains sensitive information.
What industries need to be particularly careful with Slack for security reasons?
Some organizations have more stringent data security requirements than others. For example, those in highly regulated industries such as finance or healthcare must consider their obligations under legislation such as HIPAA and SEC 17a-4 to preserve compliance certifications.
Additionally, the US National Counterintelligence and Security Center (NCSC), the Office of Economic Security and Emerging Technology (OESET), and special units within the Air Force and Navy have all recently cautioned tech companies that they face heightened information security risks from foreign state actors, who can use company tools like Slack to exfiltrate proprietary information.
For these organizations, it may be best practice to restrict Slack access to company-owned email addresses and mobile devices. In all instances, device management should be a regular part of a Slack security review.
Types of sensitive data shared on Slack
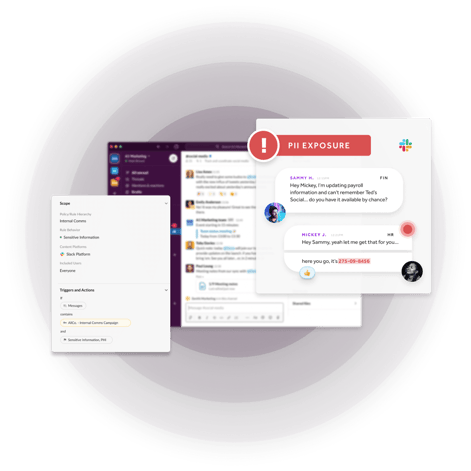
Collaboration messages contain a significant amount of sensitive data that companies need to protect. This includes regulated information like PII/PHI/PCI and unregulated — but valuable — intellectual property and other confidential communications.
- Personal Identifying Information (PII)
- Personal Health Information (PHI)
- Payment Card Industry data (PCI)
- Intellectual Property (IP)
- Mergers and Acquisitions
- Toxic, bullying and hate speech
The proliferation of this information throughout the Slack environment could lead to intense regulatory scrutiny and costly fines and penalties. Threat actors can also use confidential information to embarrass the company or cost it a business advantage. The latest research shows that 12% of employees take IP with them when they leave for another job.
The reason so much sensitive data is stored in Slack is simple: employees mistakenly believe that an enterprise-sanctioned tool is a secure repository for any work-related data. The first failure point of Slack security is in failing to coach employees on what constitutes appropriate and inappropriate information-sharing in Slack.
Aware research backs this up. One Aware customer discovered 32,000 instances of PCI/PII data being stored in Slack channels by employees who were simply trying to do their jobs.
Read the case study about detecting PII in Slack
Simply coaching employees isn’t enough. To protect company data from exfiltration in Slack, businesses need to take a proactive approach to threat management. Unfortunately, Slack does not deploy proactive data security tools as standard. Instead, businesses must implement their own security controls through the use of enterprise-grade data security integrations and third-party apps.
What are Slack’s in-built security features?
Data encryption in Slack
By default, Slack encrypts data in transit and at rest. That means Slack information held in databases or being transmitted is protected from easy exfiltration. However, unlike some other messaging apps, Slack does not offer end-to-end encryption of its data. That means any threat actor with access to the Slack server can access or exfiltrate all the information it holds. This could also increase Slack’s vulnerability to malware and other forms of attack.
End-to-end encryption is considered the gold standard of data security policies because the only people who can access the data are the sender and intended recipient(s), usually by storing the encryption keys on individual devices rather than at server-level.
✅ Data in transit encryption (aka data in motion encryption)
✅ Data at rest encryption (DARE)
❌ End-to-end encryption
Slack Enterprise Key Management
As well as data encryption, Slack also provides other data security tools. Slack Enterprise Key Management (Slack EKM) enables businesses to bring their own encryption keys to their Slack environment. This gives companies more control over how their data is encrypted, and who can access it through granular permission controls. These additional verification features can help combat common external attacks, such as phishing scams, and lock out a hacker the moment they are detected.
Slack audit logs
If a business needs to perform forensic investigations in Slack, Audit Logs provide a useful starting point. These logs record all the actions users take within Slack and create custom monitoring tools using the Audit Logs API. However, businesses cannot see the messages employees send in Slack and audit logs don’t enable proactive threat hunting. That functionality requires the addition of a third-party Slack app for data loss prevention (DLP) and/or eDiscovery.
Other Slack data security features
Slack can give users more control over who gains access to the environment, and for how long, through security tools like session limits, two-factor authentication, multi-factor authentication and single sign-on (SSO). These settings can make it harder for threat actors to gain access to a corporate Slack account and reduce the time a hacker has to act.
In summary, Slack provides a secure workspace for businesses using industry-standard data encryption in transit and at rest. However, to gain a full picture of what is happening within an enterprise Slack environment companies must pair native Slack security capabilities with more powerful cybersecurity platforms.

How many users does Slack have?
Is Slack secure for business use?
How many integrations does it support?
Learn the answers to these questions and more
What are the different security concerns with Slack?
When it comes to protecting enterprise Slack environments from data exfiltration, there are multiple types of threat to consider. Each requires its own proactive management strategy.
Download the quick checklist to start preventing data exfiltration in Slack
Slack platform security threats
Security risks within Slack itself can threaten enterprise data security by allowing hackers to breach the workplace Slack environment. Slack data exfiltration by hackers made headlines thanks to the Uber breach, where Slack messages were explicitly targeted and stolen by the hacker.
Why would hackers steal Slack data? As Aware research has uncovered, Slack ecosystems can be packed with confidential information and company secrets. Even if the hacker never uses that information, it can still cost the business a significant amount in fines and penalties.
The average cost of a breached record was $164 according to research by IBM in 2022. When 1:166 messages in Slack contain confidential information, that means every new message typed into your Slack environment adds another dollar to the total cost of your risk exposure — and just 5,000 employees will send 30 million Slack messages each year.
Slack insider threats
The other concern for modern businesses when using Slack, or any other collaboration tool, is insider threats. The Ponemon Institute found that insider threats continue to increase, with the cost to businesses at an all-time high. It takes the average organization 85 days to identify and contain an insider threat, at a cost of $15.38 million per incident.
Insider threats occur through negligence or malice. The majority of threats aren’t intentional. Carelessness accounts for 56% of all insider threat incidents, usually because employees have shared sensitive information in the wrong channels. Compliance violations via sharing of PII/PCI information within Slack channels is a prime example of an insider threat caused by carelessness.
Malicious insiders are rarer but do much more harm to the enterprise. Because they have been invited into the workspace, they can be harder to detect and know where to look for valuable information. And because Slack enables private channels and direct messages and syncs across multiple devices, a malicious insider can also use Slack to send confidential information to themselves and gain access to it later from a private device, circumventing firewalls and other data security controls.
- The average malicious insider exfiltrates 80,000 business records
- Attacks by malicious insiders take an average of 284 days to identify and contain
- The average cost of a malicious data breach is $4.18 million
Source: IBM
Risks with third-party integrations
One of the key features Slack offers is its ability to integrate with other applications, but this can also open a gap in security. Slack does not vouch for the security of the apps listed in its directory, so organizations are responsible for evaluating the apps they connect with. Poorly configured apps could lead to a data leak.
Many third-party apps also require the ability to read/write messages, access files for sharing, or create new channels. These permissions open Slack to vulnerabilities that can lead to data exfiltration. There’s the additional risk of malware with unvetted third-party apps.
To mitigate this risk, companies need strict policies for third-party app approval when integrating with Slack that include limiting app permissions to the minimum required and monitoring integrated apps for suspicious activity.
Phishing
Phishing scams target popular collaboration tools like Slack and Teams because these platforms allow third parties to integrate into their channels. Attackers pose as Slack users to send group chat invites and then trick users into downloading malware payloads into the victim companies’ systems.
It’s happened multiple times through Teams, which shares this vulnerability with Slack. The trouble with phishing scams is training employees to recognize them. When they appear to come from inside enterprise-approved platforms, they’re harder to spot.
Allowing access to external users
Slack Connect gives employees the ability to work collaboratively with people outside the organization. However, opening the platform up to these users poses a risk to companies’ security in a few ways. One is a simple matter of access. Providing contractors and other external users the minimum permissions required to complete the project is one best practice. Monitoring their activity is also key because users in Slack can change their profile picture and name to appear as if they’re another user within the organization. Malicious actors can infiltrate an organization this way if they have intentions for harm.
External users bring their own devices to the table, and these provide another point of Slack vulnerability. Implementing strict controls as well as monitoring their app usage while working on the project is key to maintaining data security. Once an engagement is finished, promptly deprovisioning their access can further reduce the chance of a data breach.
Download the whitepaper to get more insights and discover how businesses can mitigate top risks using compliance adherence, DLP and federated search to prevent data exfiltration in Slack.
Best practices for improving Slack security
So what can businesses to do mitigate risks of Slack platform security threats? To detect and contain PII and prevent data exfiltration from Slack, security teams should:
- Introduce access safeguards: Follow best practices to take control of who can access the Slack workspace by instituting access control safeguards such as SSO or Slack EKM.
- Remove sensitive data from Slack: Institute proactive retention policies to identify and remove compromising information from Slack so it’s never available for a hacker to exfiltrate.
- Monitor for compliance: Establish rules-based policies that search for RegEx and keywords in near real time for around-the-clock compliance.
- Create a culture of data protection: Frequently train employees on what is and isn’t appropriate information to share in Slack and reinforce training with automated real-time coaching when policy violations are detected.
- Create an audit log with backup: Maintain an immutable archive of Slack user conversations, including revisions and deletions, so you always have oversight of the big picture.
- Have the right tools for the job: Deploy a federated search program that can quickly surface Slack messages and filter by multiple parameters to increase relevancy and accelerate eDiscovery.
- Understand your vulnerabilities: Use AI analysis with natural language processing to identify toxicity and negative sentiment that can indicate areas of enhanced risk.
- Use 2-factor identification: Having users verify their login ensures a hacker cannot access the work environment even if the user’s password is compromised.
- Use email and domain verification: Verifying emails and domains before granting users access into workspaces is another way to confirm their identities. It’s particularly useful against phishing attacks.
- Implement single sign-on security: Have users verify their login through a centralized identity provider like Azure Active Directory or Okta. This removes the complication of juggling passwords, which employees prefer.
- Provide Slack guest accounts: When working with external contractors or temporary partners, guest access allows admins easy control over permissions. It’s also easy to remove the provision when the project ends.
- Limit session durations: Automatically log idle Slack users out, so unattended Slack interfaces are less likely to be available to unauthorized users.
- Deactivate old accounts: Review accounts regularly to ensure the roster of current users is up-to-date. Revoking access to dormant accounts reduces the risk of unauthorized access to those who should no longer have it.
- Limit Slack bots and apps: Carefully vet the third-parties with access to Slack. Grant access only to trusted and necessary enhancements, and periodically review their permissions.
In all Slack workspaces, admins should implement robust employee training in security practices to enforce the organization’s security standards. Employees are both the biggest risk and greatest asset of any security program and are on the front lines of protecting data in Slack.
How Aware strengthens Slack security to safeguard your data
- Built-in privacy and compliance controls for Slack
- Powerful federated search of conversation data in context
- Granular control of data based on role, group, channel, location and more
- Real-time compliance adherence and behavioral analysis
Aware business intelligence platform is an industry-leading compliance and security solution for Slack and GovSlack. Aware enables enterprise businesses to protect sensitive and restricted data in Slack and mitigate top risks in collaboration datasets.
Learn more about how to get data retention, eDiscovery, and DLP for Slack with Aware
Using the Aware integration for Slack, organizations can avoid costly fines and penalties by implementing real-time compliance adherence and moderation that protects data across the Slack environment.
This Aware client has done just that. With seasonal hires who are less familiar with Fair Credit Reporting Act violations, this tech company needed a solution that covered Slack alongside their existing email compliance. Aware helped them develop policies and alerts in real-time for PII shares within Slack. The automated alerts save them time and reduce the risk of fines and regulatory action.
Use AI and machine learning-infused insights, teamed with best-in-class natural language processing, to detect policy violations in near real time. Tackle security issues from every angle by automating the removal of unauthorized information sharing, notifying stakeholders and coaching employees the moment a violation is detected. And become proactive about threat detection and data compliance by deploying groundbreaking sentiment insights that identify pockets of negativity or toxicity within the enterprise.