Acceptable Use Policy: What It Is and Why You Need It
by Aware
How many digital tools, apps, and platforms are in use across your organization today? How many devices connected to your network? Acceptable Use Policies (AUPs) provide comprehensive guidelines on what is and is not acceptable within an organization's computer systems, networks, software, and other technology assets. Whatever your business’s industry or size, implementing an effective AUP is essential in navigating the intricacies of technology usage while safeguarding the interests and integrity of your organization.
Contents
- What is an Acceptable Use Policy?
- Examples of an Acceptable Use Policy
- What businesses require Acceptable Use Policies?
- The benefits of AUPs
- The components of a robust Acceptable Use Policy
- Best practices for creating an Acceptable Use Policy
- How to enforce an acceptable use policy
- Aware: AI-powered acceptable use enforcement
What is an Acceptable Use Policy?
An Acceptable Use Policy (AUP) is a set of guidelines and rules established by organizations to define approved usage of their computing resources. This policy outlines the expectations for how employees and other authorized users should interact with these resources.
AUPs articulate the proper and improper ways to use an organization's computer network, including internet access, fair use, and unacceptable use. They act as a code of conduct for individuals granted access to these resources, ensuring that they use them responsibly and in alignment with the organization's goals.
The primary purpose of an AUP is to protect the organization's interests, assets, and reputation. By establishing clear guidelines, an AUP helps prevent misuse, unauthorized access, and other behaviors that could compromise the organization's information and employees. Additionally, it serves as a tool for promoting company security policies and ensuring a productive technology environment.
Acceptable Use Policies should be clearly communicated to new employees during the onboarding process and made available in the employee handbook for future reference. While most AUPs focus on acceptable use of the internet and technology assets, some businesses also define acceptable use in other areas of the company.
Examples of an Acceptable Use Policy
Because AUPs cover a broad range of technologies and assets, companies may choose to have a single encompassing document or address responsibilities separately for hardware vs. software, for example. Some examples of Acceptable Use Policies include:
- Internet Usage Policy: Outlining acceptable behavior and activities when using the organization's wi-fi, VPN, or internet service providers.
- Email Policy: Defining acceptable use and behavior regarding the organization's email system, including rules for communication and content. AUPs may also cover the use of personal email on company-owned machines.
- Bring Your Own Device (BYOD) Policy: Outlining rules and security measures when employees use their personal devices for work purposes.
- Data Protection Policy: Defining how sensitive data is handled, stored, and protected to ensure compliance with privacy regulations.
- Remote Work Policy: Providing guidelines for employees working outside the traditional office environment, covering issues like security, productivity, and communication.
- Software Usage Policy: Describing the appropriate use and installation of software on company devices to maintain security and compliance, including if company software can also be used for personal use.
- Harassment and Discrimination Policy: Addressing behavior expectations related to harassment and discrimination, promoting a safe and inclusive work environment.
In addition, some companies may require employees to sign AUPs that go beyond the scope of the business’s IT resources, particularly if employee behavior can bring the company itself into disrepute. Common examples include social media guidelines and company travel policies.
What businesses require Acceptable Use Policies?
AUPs are commonly implemented by a variety of businesses, including for-profit and non-profit companies, as well as educational institutions and government agencies. Any workplace that deals with IT—from company emails to scheduling apps—can benefit from creating Acceptable Use Policies that outline how employees should interact with the technology.
It is in the best interests of both the business and employees to agree on what constitutes acceptable use in order to maintain a secure and efficient workplace.
The benefits of AUPs
Having Acceptable Use Policies in place is important for offering protection on a number of fronts. Firstly, AUPs can reduce cybersecurity threats by guiding employees on how to keep their technology and data secure. Equally, AUPs ensure the organization and its employees comply with relevant laws and regulations, reducing the risk of legal action related to technology use and explicitly prohibiting illegal activities such as downloading pirated content or deleting messages exchanged between regulated employees.
In addition to security and compliance, Acceptable Use Policies can create efficiencies and deliver cost savings by limiting data usage and storage. Examples of such policies include download limits, file type restrictions, and specifying when and where to back up company data.
Finally, APUs can have a positive impact on productivity by minimizing distractions such as social media use during work hours.
The components of a robust Acceptable Use Policy
An effective AUP comprises several components, such as:
- Device Usage Expectations: Clearly define how workplace devices may be used and specify the systems to which the AUP applies.
- Comprehensive Restrictions: Provide a detailed list of prohibited activity to guide users on acceptable behavior.
- Software Installation Guidelines: Establish guidelines on the installation and maintenance of software to prevent security risks.
- Non-Employee Usage: Specify how non-employees can use company resources and the responsibilities employees have for safeguarding property from unauthorized access.
In addition to detailing what activities are permitted and prohibited, a comprehensive AUP should also include information about how the company will monitor and enforce acceptable use, and any potential consequences or disciplinary action employees could face for non-compliance.
Best practices for creating an Acceptable Use Policy
Writing an AUP is usually a team affair to ensure all aspects of the policy are considered and covered. Some of the stakeholders to involve include:
HR and People Teams — to provide comprehensive training on the AUP during onboarding and periodically communicate policy changes to all employees.
Comms or Marketing Teams — to craft the AUP in clear, easy-to-understand language, avoiding jargon and ambiguity.
IT Teams — to deliver a list of covered hardware and software and identify areas of particular risk.
Legal and Compliance — to advise on any obligations the organization and/or its employees have to fulfill.
By engaging leaders from different areas of the business, organizations can create and maintain an AUP that effectively guides users and protects the integrity of their technology resources.
How to enforce an Acceptable Use Policy
Enforcing an Acceptable Use Policy begins with communicating clearly with employees. They must understand their responsibilities and obligations and be clear on how to abide by company policy. Employees should also receive training on what the policies are and how to abide by them, for example educating on how to set strong passwords, or what to do if they suspect a phishing attack.
Employee training isn’t a one-and-done activity but should be repeated periodically to ensure the lessons stick. Clearly articulating the reasoning behind AUP restrictions can also enhance compliance by helping employees understand the why behind the rules they have to follow.
In tandem with employee training, it’s important for businesses to use tools to monitor and enforce acceptable use within the workplace. These might include DLP solutions to identify unauthorized devices or apps accessing the company network, or content moderation tools to detect sensitive data or inappropriate language in employee chats. These tools can protect the company from security incidents and data breaches that could endanger the corporate network or lead to the loss of confidential information and intellectual property.
Aware: AI-powered acceptable use enforcement
Aware supports acceptable use enforcement with AI-powered automations designed for your company’s fastest-growing and most complex data set: collaboration conversations. The digital workplace has created hundreds of tools and applications where employees can talk—everything from messaging apps like Slack and Teams to productivity and storage suites like Google Drive and enterprise social networks like Workplace from Meta.
Managing all the different ways employees can violate AUPs within those data sets without a dedicated solution designed for that purpose is slow and complex, requiring significant time in manual review.
What risks do collaboration tools contain?
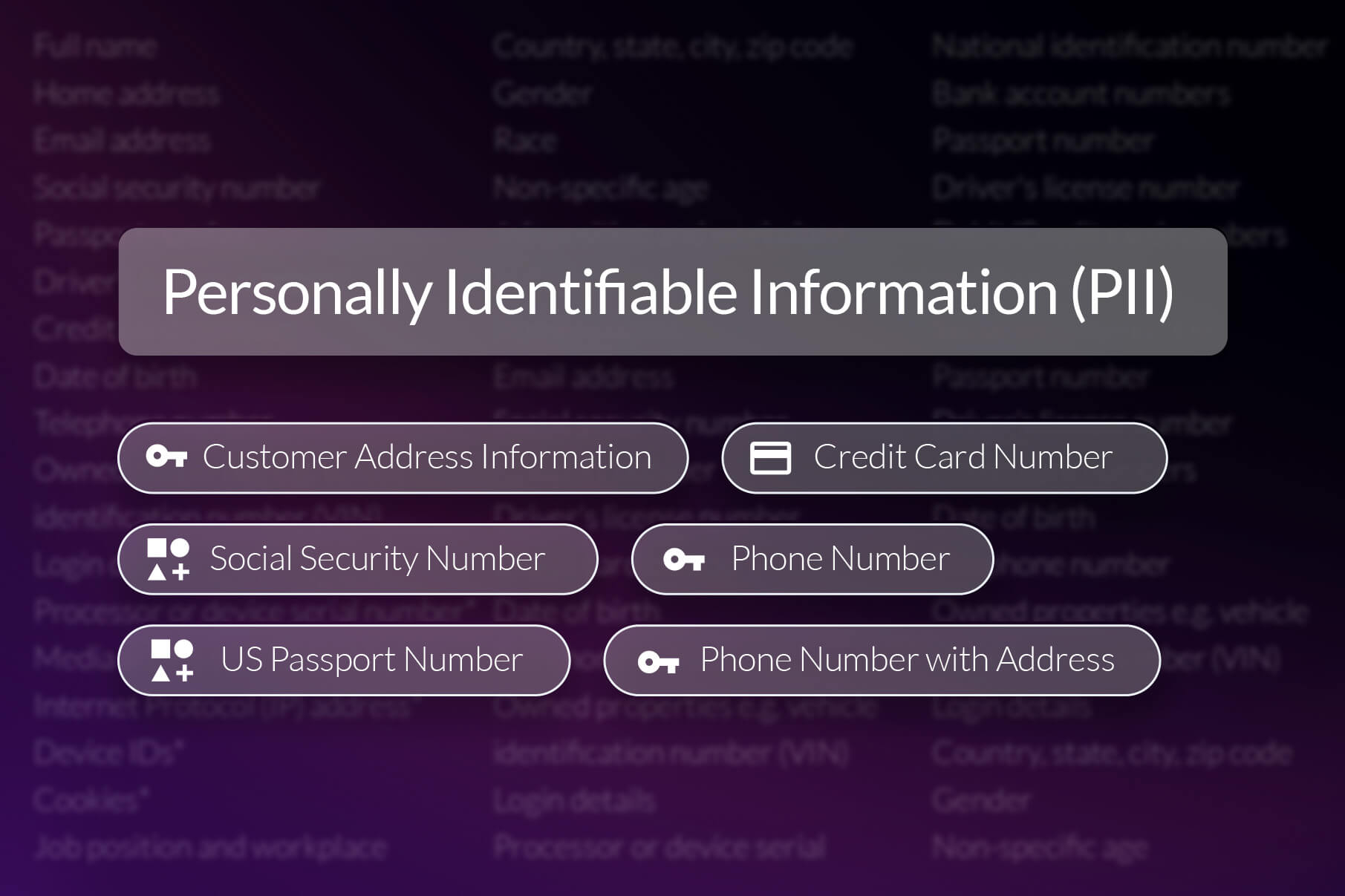
- Information security — How would you spot an employee using Slack to sync a confidential file to their personal device?
- Compliance — Did you know digital collaboration tools are included in retention requirements of legislation like SEC 17a-4?
- Network performance — Employees sent over 18 trillion messages in 2022. What is that data exhaust costing you?
- Search and investigations — eDiscovery and internal investigations are complicated by the sheer scale of collaboration data and reduced visibility into all the messages sent in these tools.
- Company culture — Instant messaging tools make it easy for bullying, harassment, and toxicity to go unnoticed until they poison the entire organization.
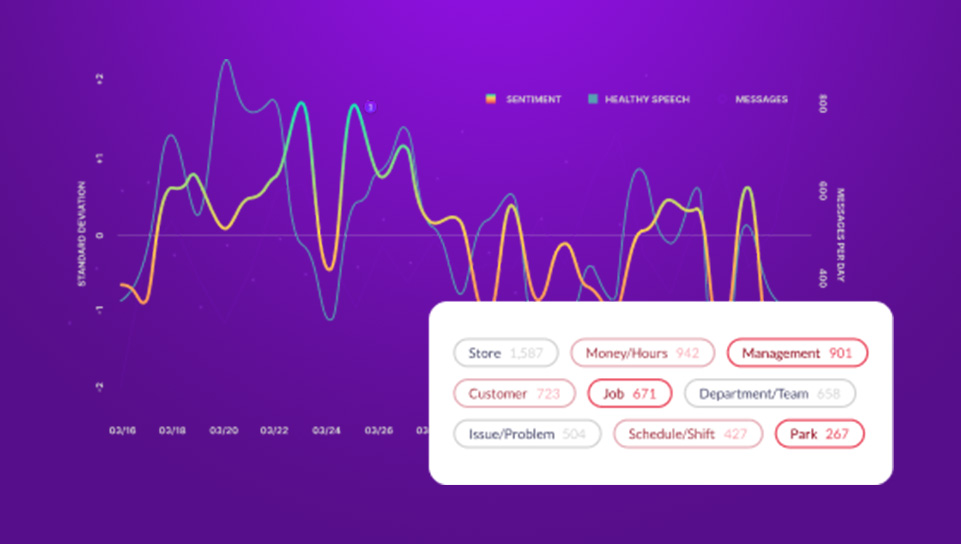
Aware’s platform takes a centralized approach to consolidating and moderating collaboration tool conversations, performing real-time analysis that detects more instances of violations with fewer false positives. AI/ML workflows further measure sentiment and toxicity within the workplace, helping leaders to get ahead of shifts in company culture that put the business and its data at risk. Using Aware you can:
- Search by keyword, regex, and more using customizable automations that run 24/7
- Look beyond text for violations such as NSFW images and sensitive data in screenshots
- Protect all your data with secure uploads and role-based access (RBAC)
- Accelerate existing processes using Aware’s Workflow Library
- Automatically coach employees in real time to mitigate future policy incidents
Aware’s proprietary natural language processing (NLP) technology empowers more businesses to perform effective acceptable use moderation and monitoring by identifying potential violations in near real time and taking automated action to coach employees on best practices.
Using Aware, businesses can improve their overall risk posture, support proactive compliance, and protect their company culture by enforcing continuous acceptable use in workplace collaboration tools.
Learn more about how Aware supports compliance teams across the enterprise.